In today’s increasingly digital landscape, Australian businesses are more vulnerable than ever to cyber threats. Whether it’s ransomware, data breaches, or phishing attacks, the risks are real and growing. The Australian Cyber Security Centre (ACSC) has developed a set of eight critical strategies—known as the Essential 8—to help organisations protect themselves against these evolving threats. In this blog post, we’ll explore what the Essential 8 is, why it’s vital for your business, and how you can implement these strategies to build a robust cybersecurity defence.
What is the Essential 8?
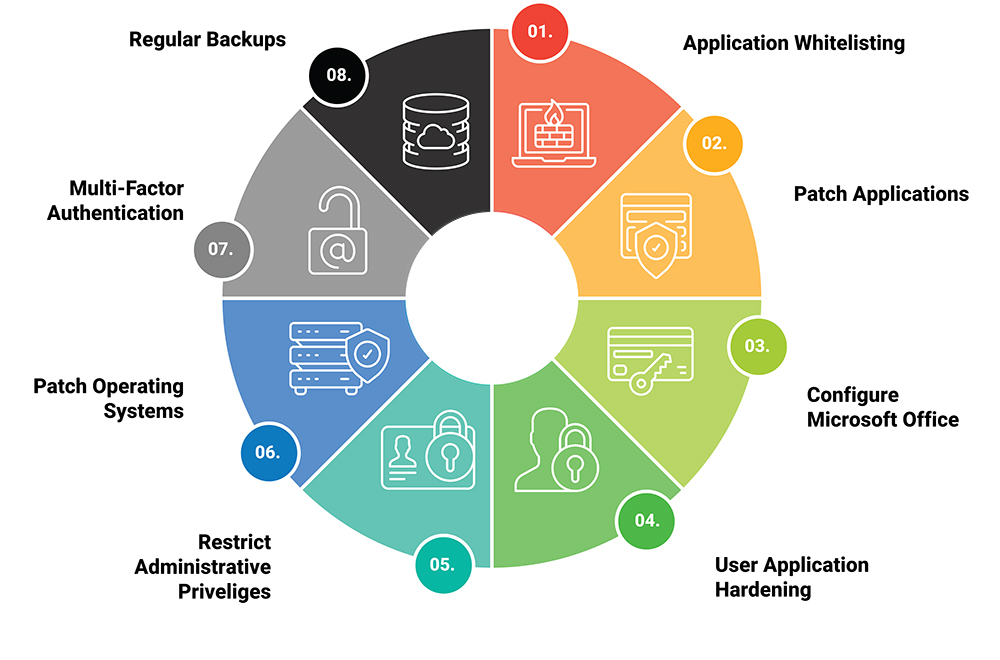
The Essential 8 is a prioritised list of mitigation strategies recommended by the ACSC. These strategies are designed to help businesses reduce their exposure to cyber attacks by addressing common vulnerabilities and weaknesses within their systems. The Essential 8 is not just for large corporations; it’s scalable and adaptable to suit businesses of all sizes, making it a cornerstone of cybersecurity across various industries.
The 8 Strategies Explained
- Application Whitelisting: This strategy involves creating a list of approved applications that are allowed to run on your systems. By only permitting known and trusted software to execute, you can significantly reduce the risk of malicious programs infiltrating your network.
- Patch Applications: This strategy involves creating a list of approved applications that are allowed to run on your systems. By only permitting known and trusted software to execute, you can significantly reduce the risk of malicious programs infiltrating your network.
- Configure Microsoft Office: Macros in Microsoft Office documents can be exploited to deliver malware. By configuring macro settings to only allow trusted macros, you can protect your business from this common attack vector.
- User Application Hardening: This involves disabling or limiting certain features within applications that are commonly targeted by attackers, such as JavaScript in PDFs. Hardening your applications makes it more difficult for hackers to find and exploit weaknesses.
- Restrict Administrative Privileges: Limiting administrative privileges is crucial to reducing the potential impact of a cyber attack. By ensuring that only essential personnel have admin rights, you can prevent attackers from gaining full access to your systems.
- Patch Operating Systems: Just like applications, operating systems need regular updates to fix security vulnerabilities. Ensure your operating systems are patched promptly to protect against the latest threats.
- Multi-Factor Authentication (MFA): MFA adds an additional layer of security by requiring users to provide two or more verification factors to gain access. This dramatically reduces the risk of unauthorised access, even if passwords are compromised.
- Daily Backups: Regular backups ensure that your business can quickly recover from a cyber incident, such as ransomware. Backups should be stored securely and tested regularly to ensure they can be restored when needed.
Why the Essential 8 is Vital for Your Business
Implementing the Essential 8 is not just about ticking boxes; it’s about creating a resilient defence system that can protect your business from the wide array of cyber threats that exist today. By adopting these strategies, you can:
- Reduce Your Risk: The Essential 8 addresses the most common and effective methods used by cybercriminals. By following these guidelines, you’re significantly reducing the likelihood of a successful attack.
- Ensure Compliance: Many industries have regulatory requirements that mandate robust cybersecurity measures. The Essential 8 provides a clear framework that can help your business meet these obligations.
- Protect Your Reputation: A cyber attack can cause significant damage to your business’s reputation. Implementing strong security measures demonstrates to your customers and partners that you take their data protection seriously.
- Minimise Costs: The financial impact of a cyber-attack can be devastating. By preventing incidents from occurring in the first place, you can save your business from costly disruptions and potential fines.
How to Implement the Essential 8
- Assess Your Current Security Posture: Start by evaluating your current cybersecurity measures. Identify gaps and weaknesses that need to be addressed according to the Essential 8 guidelines.
- Prioritise the Strategies: Depending on your business’s specific needs and resources, you may choose to prioritise certain strategies over others. For example, if your business heavily relies on third-party software, patching applications might be a top priority.
- Engage with Cybersecurity Experts: Implementing the Essential 8 can be complex, especially for businesses without in-house cybersecurity expertise. Consider partnering with cybersecurity professionals who can guide you through the process and ensure that the strategies are correctly applied.
- Regularly Review and Update: Cybersecurity is not a one-off task. Regularly reviewing and updating your security measures is crucial to staying ahead of emerging threats. Make sure that your implementation of the Essential 8 evolves as your business grows and the threat landscape changes.
Conclusion:
The Essential 8 framework is a powerful tool that can help Australian businesses protect themselves against the ever-present risk of cyber attacks. By understanding and implementing these eight key strategies, you can build a robust defence system that not only meets regulatory requirements but also safeguards your business’s data, reputation, and financial stability. Don’t wait for a cyber-attack to happen—start implementing the Essential 8 today and ensure your business is prepared for whatever challenges lie ahead.