Ransomware is no longer a rare emergency. It is a predictable business risk that you can plan for and control. With the right preparation, you can reduce the chance of an incident, limit the blast radius if one occurs, and recover quickly with minimal downtime. This guide gives you a practical, step by step plan tailored to Australian organisations, from employee awareness through to response planning and secure backups.
First, set your baseline and priorities
Preparation starts with visibility. You cannot protect what you cannot see.
- Map your critical assets. Identify the systems, applications, and data that matter most to operations, customers, and compliance. Include cloud apps and third party integrations.
- Review your controls against a framework. Many Australian businesses align with the Essential 8, ISO 27001, or NIST. A focused review highlights the biggest uplift for the least effort.
- Assess your threat paths. Look at email, remote access, supply chain, and privileged accounts. These are common paths ransomware operators use to gain initial access and move laterally.
If you need independent verification, scheduled testing gives clear evidence of where to invest. Regular assessments, including external, internal, and cloud security reviews, will surface configuration weaknesses and patching gaps before an attacker does.
Build your human firewall with targeted awareness
Most ransomware campaigns begin with social engineering or a malicious attachment. Your people are the first line of defence, so make awareness practical and ongoing.
- Run short, role based sessions that show what to look for and what to do when something looks off.
- Reinforce with realistic exercises. A well designed phishing simulation helps you measure risk and coach those who need support.
- Make reporting easy. A one click report button in the email client speeds up internal escalation and containment.
- Keep it positive. Celebrate safe behaviours, do not shame mistakes. You want rapid reporting, not silence.
If you want a structured program, consider online security awareness training that blends micro learning with periodic tests. This creates a rhythm of vigilance and ensures new starters get up to speed quickly.
Strengthen your technical controls where it counts
Ransomware thrives on unpatched systems, weak identity controls, and poor segmentation. Focus on the controls that most reliably reduce risk.
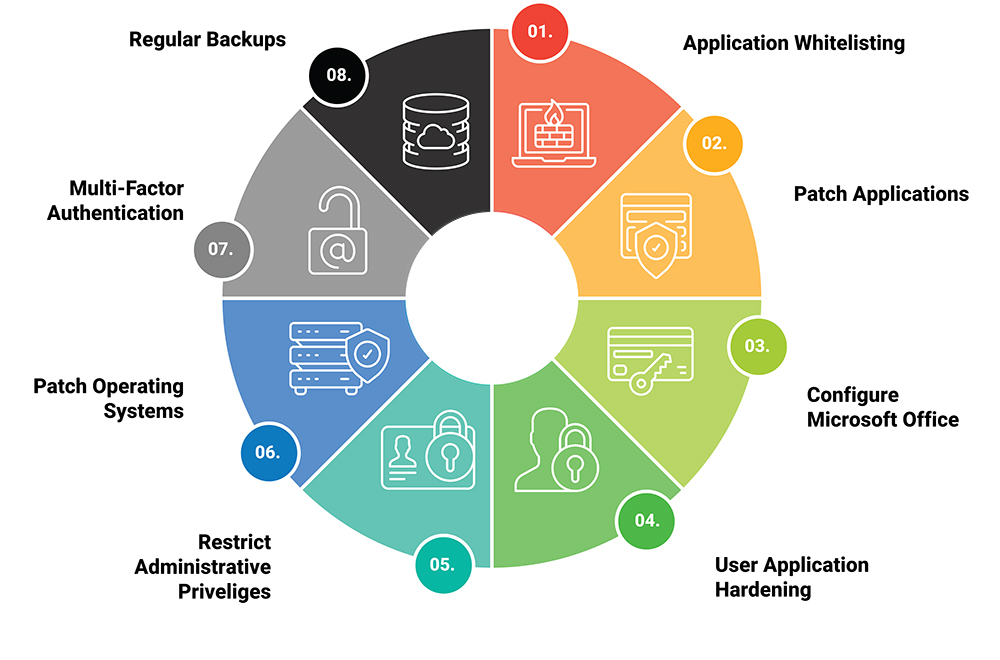
- Patch and harden. Maintain an inventory, automate updates where possible, and prioritise internet facing assets and high value servers.
- Protect identities. Enforce multi factor authentication on email, VPN, privileged accounts, and remote management tools. Apply conditional access policies and least privilege.
- Monitor endpoints. Use modern endpoint detection and response to identify suspicious behaviour, isolate infected devices, and support rapid investigation.
- Filter email. An email security gateway that scans links and attachments, with URL rewriting and sandboxing, will remove a large portion of malicious content.
- Segment networks. Separate user workstations from servers, and ring fence backups and critical systems using firewall rules and access controls.
- Manage vulnerabilities continuously. Scan routinely, track remediation, and verify fixes. Integrate findings into change management so issues do not linger.
Independent validation helps confirm these controls are working. Routine penetration testing, including internal scenarios, often uncovers privilege escalation paths or misconfigurations that automated tools miss.
Backups that actually save your business
Backups are your seatbelt. They must be resilient, recent, and recoverable.
- Follow the 3-2-1 principle. Keep three copies of data on two different media types, with one copy offsite or immutable.
- Secure the backup plane. Use separate credentials and networks for backup infrastructure. Apply MFA to consoles and restrict admin access.
- Test restores. Run regular recovery drills for a sample of critical systems and data. Measure recovery time and document step by step procedures.
- Snapshot the right things. Include configuration data, domain controllers, and SaaS exports where possible. Do not rely on storage replication alone, since it can replicate encryption.
A strong backup strategy turns a potential ransom event into an IT recovery task. Testing is the difference between confidence and hope.
Create a clear, rehearsed incident response plan
A comprehensive response plan is essential because speed and coordination determine impact. During a ransomware event, every minute counts and uncertainty is expensive.
- Define roles and decision rights. Name your incident lead, communications owner, legal contact, and business representatives. Include after hours details.
- Standardise workflows. Document steps for detection, containment, eradication, and recovery. Include playbooks for common scenarios such as credential theft or mass encryption attempts.
- Prepare communications. Draft internal and customer notifications, media holding statements, and supplier outreach templates to avoid delays.
- Pre stage tools and access. Ensure logging, forensic acquisition tools, and privileged access are in place and tested. Store critical runbooks offline.
- Rehearse with table top exercises. Walk through realistic scenarios with IT, executives, and key vendors. Update the plan based on findings.
When you have a plan, you reduce confusion, avoid duplicated effort, and protect evidence that may be required for compliance or insurance.
Practical steps to get ready this quarter
If you are wondering where to start, use this 90 day action plan.
- Weeks 1 to 2: Run a rapid risk and control review aligned to your chosen framework. Confirm your asset inventory and high value targets.
- Weeks 2 to 4: Enable MFA everywhere it is practical, tighten admin rights, and deploy or tune endpoint detection and response across all devices.
- Weeks 3 to 6: Patch critical systems and internet facing services. Implement geoblocking and conditional access for remote access where appropriate.
- Weeks 4 to 8: Launch a short cyber security awareness training campaign and a phishing simulation to baseline human risk and reinforce reporting.
- Weeks 6 to 10: Validate backups, introduce immutability, and run a recovery drill for at least two critical systems.
- Weeks 8 to 12: Conduct focused penetration testing on your external perimeter and privileged access paths. Remediate findings quickly.
- Weeks 10 to 12: Finalise your cyber incident response plan, brief leaders, and run a table top exercise.
This sequence delivers quick wins while laying the foundations for long term resilience.
How White Rook Cyber partners with you
You do not need to face this alone. A trusted partner can accelerate your progress and provide 24 by 7 vigilance.
- Awareness and culture. Our team delivers online security awareness training tailored to roles and risks, supported by a realistic phishing simulation that measures and improves behaviour.
- Visibility and hardening. We help you prioritise remediation through continuous vulnerability management and targeted testing, and we support secure configuration across cloud and on premises systems.
- Detection and response. With endpoint detection and response integrated into a monitored platform, threats are contained quickly, and evidence is preserved for recovery and reporting.
- Planning and readiness. We co design and test your cyber incident response plan, align it with your business priorities, and run exercises that build confidence.
If you want to explore specific capabilities, you can learn more about managed security services, incident response, and ransomware protection through our site. Choose what suits your maturity and industry requirements.
Key takeaways
Prevention is possible when you combine people, process, and technology. Start with visibility, train your teams, and close the most common attack paths.
- Backups must be resilient and tested. Immutability, separation, and drills are non negotiable.
- A comprehensive response plan is essential because it turns chaos into coordinated action, shortens downtime, and protects your reputation.
- Regular assessments and testing provide the evidence to prioritise and improve, so you avoid surprises.
If you are ready to reduce risk and build confidence, White Rook Cyber can help you plan, test, and operate an effective defence. Get in touch to discuss a practical roadmap tailored to your business and compliance needs.