Cyber threats keep shifting, but your approach to security does not have to. The ACSC Essential 8 gives Australian organisations a practical roadmap to reduce risk in measurable, meaningful ways. In this guide, you willlearn what the Essential 8 is, how it protects your business, what a sustainable compliance program looks like, and the steps you can take today to lift your security maturity with confidence.
What is the Essential 8?
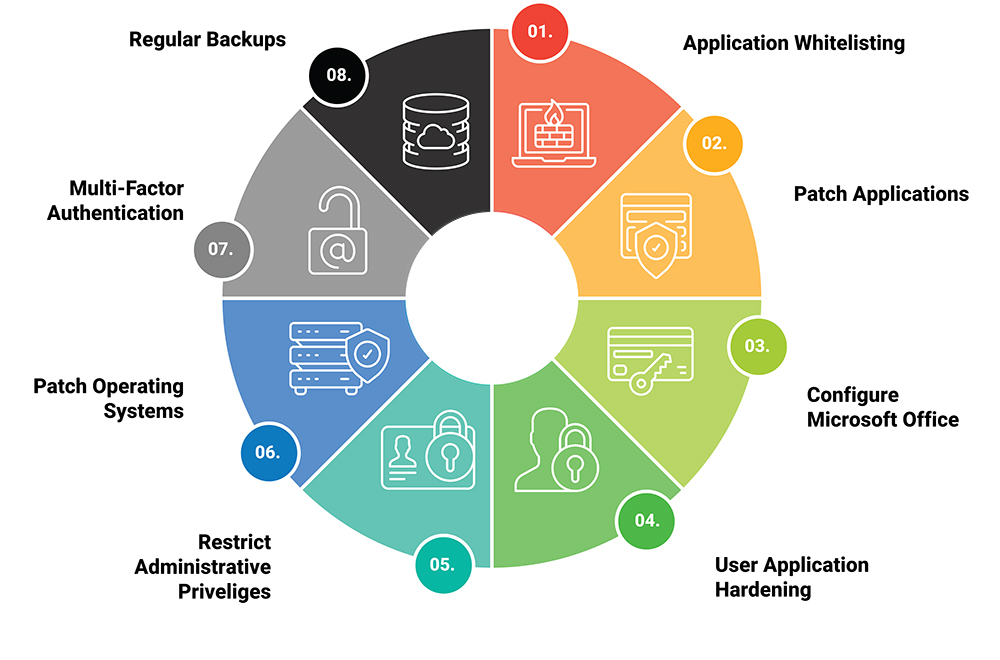
The Essential 8 is a set of eight mitigation strategies published by the Australian Cyber Security Centre. It focuses on the most common attack paths in Australian environments and provides a tiered maturity model toguide improvement over time.
The eight strategies are grouped across three goals, prevent attacks, limit impact, and recover data.
- Application control, only allow trusted applications to run
- Patch applications, remediate vulnerabilities promptly
- Configure Microsoft Office macro settings, restrict or block macros from the internet
- User application hardening, disable risky features such as Flash or unnecessary browser functionality
- Restrict administrative privileges, limit and monitor privileged access
- Patch operating systems, keep endpoints and servers up to date
- Multi factor authentication, enforce MFA for remote access and privileged actions
- Regular backups, test and protect backups to support recovery
Each control has maturity levels from 0 to 3. Level 1 addresses basic hygiene, level 2 introduces stronger prevention and monitoring, and level 3 adds robust controls suitable for higher risk profiles. Many Australian organisations target at least level 2 to materially reduce ransomware and credential theft risk.
How the Essential 8 protects your business
When implemented well, these safeguards work together to break real attacker workflows.
- Reduce initial compromise. Application control, patching, and hardening cut off common exploit paths and malware execution
- Stop privilege escalation. Restricting admin rights and enforcing MFA prevent attackers from freely moving and taking over systems
- Limit blast radius. Macro controls and user hardening reduce the chance that a single click becomes a widespread incident
- Speed up recovery. Tested backups ensure you can restore data and services quickly after a breach or ransomware event
The result is fewer incidents, lower impact when incidents occur, and clear evidence of due diligence for boards, insurers, and regulators.
A practical pathway to compliance
Compliance is not a one time project, it is a repeatable cycle. To achieve and maintain Essential 8 maturity, align your effort to these steps.
- Establish your current state
Run an independent essential 8 assessment to map maturity by control and by asset class. Inventory applications, endpoints, servers, cloud workloads, and identities. Capture exceptions and businessconstraints.
- Prioritise by risk
Focus on high value assets and high exposure systems first, such as domain controllers, remote access paths, email, and internet facing services. Tie remediation to threats you face, like ransomware, credential stuffing, or business email compromise.
- Build a practical roadmap
Create a 90 day plan for quick wins and a 12 month plan for structural changes. Define owners, budgets, and success criteria for each control. Fit work into change windows and maintenance cycles to reduce disruption.
- Implement, measure, improve
Deploy controls in phases, verify with testing, then monitor continuously. Use simple, objective measures, patch compliance rates, MFA coverage, number of local admins removed, application whitelisting coverage, backup restore test success.
- Validate regularly
Prove effectiveness through vulnerability management, configuration review, and targeted security testing. Independent testing, including penetration testing, confirms controls resist real world techniques.
Actionable steps to lift security maturity now
You do not need to boil the ocean. Start with the actions that deliver immediate risk reduction.
- Close the front door
Enforce multi factor authentication for remote access, privileged accounts, and email. Remove unused legacy protocols, disable PowerShell remoting for standard users, and tighten conditional access. - Patch with intent
Adopt a 14-day patch target for critical vulnerabilities on endpoints, and a 30-day target for servers where practical. Use ring-based deployments and track exceptions. - Reduce admin sprawl
Remove local admin rights from standard users, implement just in time access for IT, and audit privileged group membership weekly. - Control what runs
Roll out application control in audit mode, tune, then enforce. Start with high-risk devices such as jump hosts and machines used by finance or executives. - Harden user apps
Block macros from the internet, disable XLM macros, enforce Protected View, and turn off unnecessary browser plugins and risky features. - Back up like you mean it
Adopt the 3 2 1 rule, keep one immutable or offline copy, and test restores quarterly. Protect backup infrastructure with strong access controls and MFA. - Prove it works
Schedule quarterly tabletop exercises and annual external security test to volidate controls against realistic threats
If you want deeper validation, consider engaging in penetration testing to confirm that your controls hold up under pressure. You can learn more about penetration testing and why it matters here, see, penetration testing.
Ensuring ongoing compliance
Sustained compliance depends on governance and visibility. Embed these practices to keep momentum.
- Policy and standards
Translate Essential 8 requirements into internal policies and control standards. Make compliance part of change management and procurement. - Continuous monitoring
Track key metrics in a dashboard, MFA coverage, patch age, application control coverage, backup test results, privileged access changes. Integrate alerts into your SOC so drift is detected early. - Regular reviews and re testing
Reassess maturity every 6 to 12 months, or after major changes, mergers, migrations, or new systems. Validate with vulnerability scans and scenario-based exercises. - Train your people
Human error remains a leading cause of incidents. Run online security awareness training and targeted phishing simulations to lift user resilience. - Prepare to respond
Incidents will still happen. Maintain a current cyber incident response plan and test it through exercises so roles, communication, and escalation paths are clear.
How White Rook Cyber helps
White Rook Cyber supports you across the entire Essential 8 journey.
- Independent assessment and roadmap
We deliver an essential 8 assessment with clear maturity scoring and a practical remediation plan aligned to your risk and budget.
- Implementation support
Our specialists help configure application control, patch pipelines, MFA, and user hardening at scale. We also provide managed services to keep controls tuned and effective. - Validation and improvement
Through vulnerability management and targeted testing, including penetration testing services, we verify that controls are working, then adjust based on evidence. - People and process
We uplift staff capability with cyber security awareness training and reinforce learning with phishing simulation to reduce the chance of a successful lure. - Preparedness and response
Our team develops and exercises your cyber incident response plan and provides on call support if an incident occurs.
If you are unsure where to start, speak with a White Rook Cyber advisor about an essential 8 audit and a tailored roadmap for your environment.
Take the next step
The Essential 8 is achievable. With a clear baseline, a practical roadmap, and disciplined execution, you can reduce risk quickly and build resilience that lasts.
- Get your baseline, request an essential 8 assessment to understand your current maturity
- Prioritise action, focus on MFA, patching, admin rights, and backups to neutralise the biggest risks
- Validate and sustain, monitor metrics, test regularly, and train users to keep controls effective
Ready to strengthen your security posture and demonstrate compliance with confidence? Contact White Rook Cyber for expert guidance and hands on support from assessment through to ongoing improvement.
Internal resources to help you move faster:
- Learn how targeted simulations can teach staff how to prevent phishing
- Explore structured training that builds a stronger human firewall with cyber security awareness training
- See how a tested and documented cyber incident response plan keeps your business ready to act