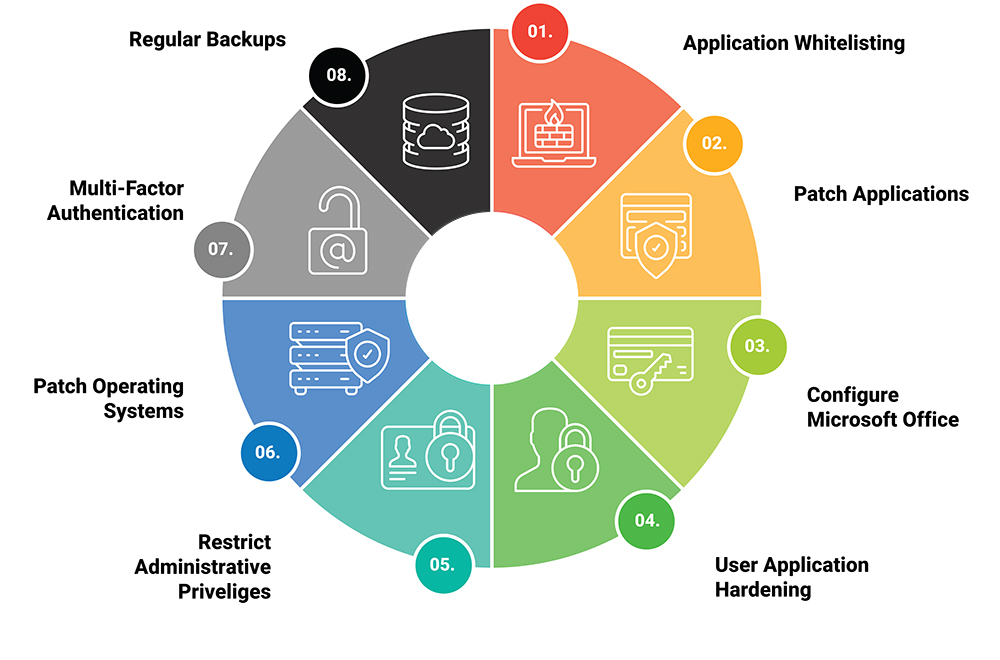
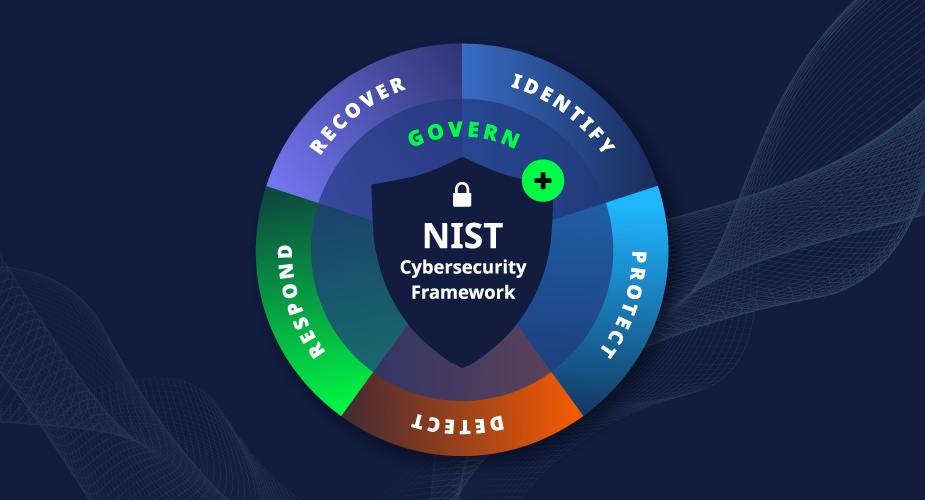
In the cyber security landscape, companies often consider both Automated Continuous Penetration Testing (APT) and External Attack Surface Monitoring (EASM) to secure their digital assets. While each approach has value, APT offers deeper insights while also ensuring a robust defence by including an EASM component and real-world attacks being actively simulated. In this article, we’ll explore why APT outperforms EASM and how it strengthens your cyber security strategy.
Understanding Automated Continuous Penetration Testing (APT)
APT is a cyber security approach that combines vulnerability detection with active exploitation, simulating how an attacker might breach your system. Unlike traditional testing, which relies on manual input, APT is continuous and automated, allowing for regular, in-depth assessments without constant human oversight. This means organisations gain proactive and detailed insights into potential real-time vulnerabilities, empowering them to stay ahead of evolving threats.
External Attack Surface Monitoring (EASM): What It Offers
EASM is focused on identifying public-facing assets — such as IP addresses, domains, and open ports — which could expose an organisation to attackers. It provides a catalogue of visible assets and flags potential security risks, helping organisations understand what’s accessible from an external viewpoint. However, EASM doesn’t test how exploitable these assets might be, nor does it simulate attacks to assess their impact.
How APT Incorporates EASM and Goes Beyond It
One of the unique strengths of APT is that it includes an EASM component to map out exposed assets. Yet, APT doesn’t stop at cataloguing; it actively attempts to penetrate, and exploit identified issues, behaving like a real hacker would. This makes APT more comprehensive and effective, as it both identifies and tests vulnerabilities:
- Asset Identification: APT begins by mapping out assets exposed to the public, similar to EASM, while ensuring that your organisation has a full view of its digital footprint.
- Simulated Exploitation: After identifying vulnerabilities, APT actively tests them, simulating real attack vectors to see how a hacker might exploit weaknesses. This provides deeper insight into potential risks and helps prioritise critical fixes.
By combining EASM’s asset discovery with real exploitation attempts, Automated Continuous Pen Testing delivers both visibility and actionable data.
Key Advantages of APT Over EASM
A. Realistic Attack Simulation
APT emulates actual attack methods to understand how a hacker would penetrate systems, providing insights that go beyond surface-level monitoring. This approach identifies weaknesses in ways EASM cannot, helping security teams develop more effective defensive measures.
B. Proactive Risk Mitigation
APT takes a proactive approach by continuously identifying and attempting to exploit vulnerabilities. This helps organisations identify critical issues before attackers can, thus preventing breaches rather than simply monitoring for them.
C. Compliance and Detailed Reporting
APT generates comprehensive reports that meet various compliance standards, such as NIST and the Essential 8. These reports don’t just list exposed assets but detail the impact of vulnerabilities and offer actionable remediation steps, making them invaluable for audit readiness and ongoing compliance.
Why Choose APT for a Stronger Cyber Security Strategy?
While both EASM and APT have roles to play in Cyber Security, APT’s combination of asset discovery and active exploitation makes it the superior choice for comprehensive protection. By simulating real-world attack scenarios, APT allows organisations to gain a complete view of their security posture, prioritize remediation, and prevent potential threats before they become breaches.
Conclusion: Protecting Your Digital Assets with APT
APT is an invaluable tool for organisations looking to stay ahead of threats. By integrating EASM into a more comprehensive testing framework, APT provides both visibility and actionable intelligence. Its active exploitation capabilities go beyond the scope of EASM alone, empowering companies to strengthen their defences with a proactive, real-world approach.
For organisations serious about Cyber Security, APT offers peace of mind and a powerful defence against evolving threats.
You can find out more about our APT offering here, or contact us for a confidential no-obligation chat about your organisation and cyber security concerns.